Pricing for Microsoft Sentinel can be challenging to understand. The information is scattered across multiple links, making getting lost in the details easy. At a high level, the pricing for Microsoft Sentinel is simple: You pay for every gigabyte ingested into and out of the Log Analytics workspace. However, there […]
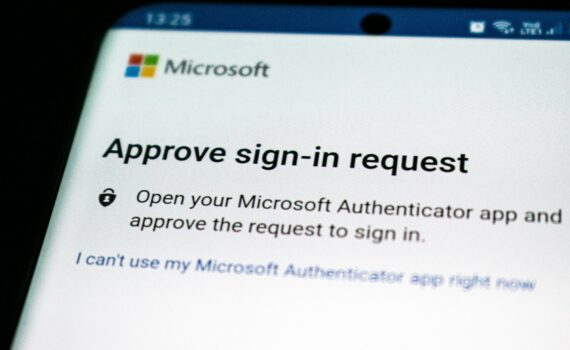
Muti-Factor Authentication is a necessity. We aren’t arguing against that. Quite the opposite. We highly recommend it. Today, we want to outline how malicious actors can bypass your MFA controls using relatively simple techniques. Some of these techniques can compromise your employees without anyone ever knowing. So, Is MFA enough? Let’s […]
You may have heard of data models. Maybe you haven’t. Regardless: Data models are a high-level topic that you’ll see thrown around. Sometimes, people claim them to be a utopian solution. Other times, people describe them as an incredibly complex topic. We will help you understand Splunk data models and […]
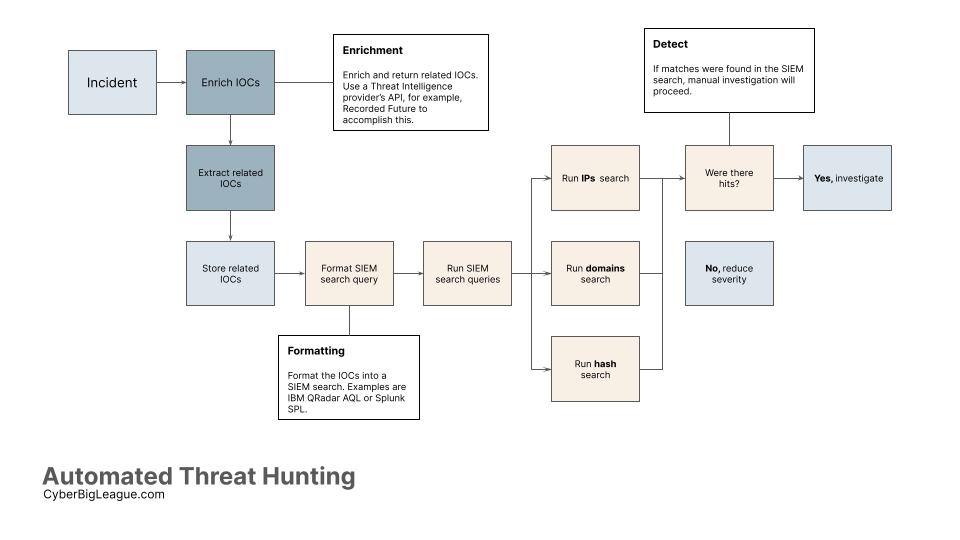
Today, the goals of maturing Security Operations teams require modest but valuable automation. In this sense, few but impactful areas of threat hunting can be automated. One is IOC enrichment, which uses various threat intelligence provider integrations/apps within your SOAR or SIEM platforms. The second area would be taking this […]